For as long as systems have been validated, risk is an inherent part of the process. Although validation engineers have been drafting risk assessments since the beginning of computer systems validation, many do not understand how crucial this process is to the overall validation process.
Risk management and validation go hand-in-hand. The ISPE GAMP 5® (“GAMP 5”) methodology is a risk-based approach to validation. GAMP 5 recommends that you scale all validation life cycle activities and associated documentation according to risk, complexity and novelty. As shown in the figure below, the key drivers for GAMP 5 is science-based quality management of risks.
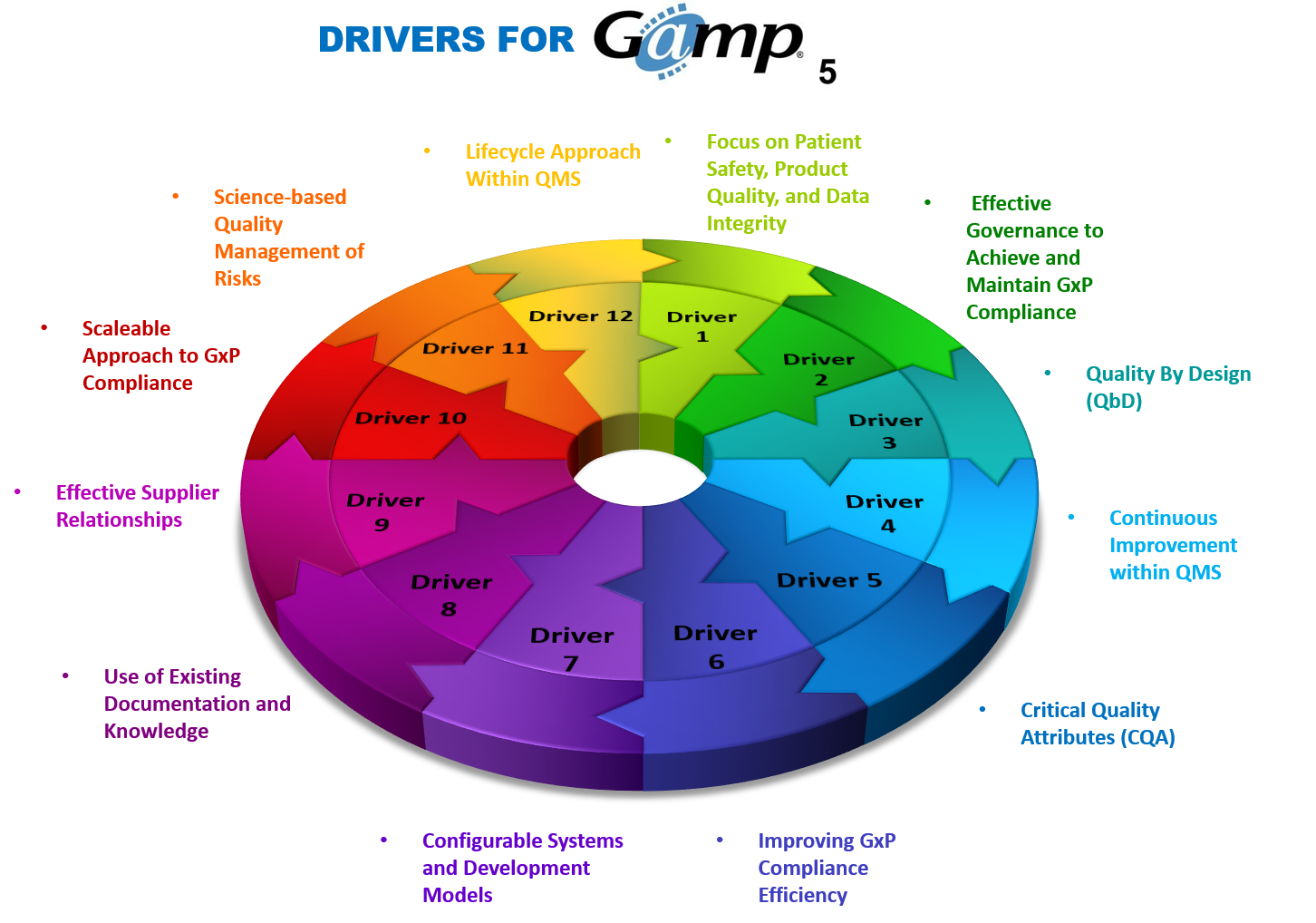
From a systems perspective, quality risk management, according to GAMP 5 is “…a systematic approach for the assessment, control, communication, and review of risks to patient safety, product quality, and data integrity. It is an iterative process applied throughout the entire system life cycle…” The guidance recommends qualitative and quantitative techniques to identify, document and manage risks over the lifecycle of a computer system. Most importantly, they must be continually monitored to ensure the on-going effectiveness of each implemented control.
Risk assessments may be used to drive the validation testing process. In our practice, we focus on critical quality attributes and four types of risks:
- Business Risks
- Regulatory Risks
- Technical Risks
- Cybersecurity Risks
The last type of risk, cybersecurity risks, is one that has not gotten a lot of attention from validation engineers and is not explicitly mentioned in GAMP 5. However, this type of risk represents a clear and present danger to ALL systems, not just validated ones. Cyber threats are real. Large-scale cybersecurity attacks continue to proliferate across many enterprises and cyber criminals are broadening their approaches to strengthen their impact. You need to look at a holistic approach to risk that not only includes the traditional risk assessment from GAMP as highlighted in the figure below but one that includes and incorporates cybersecurity as a real threat and risk to validated systems environments.
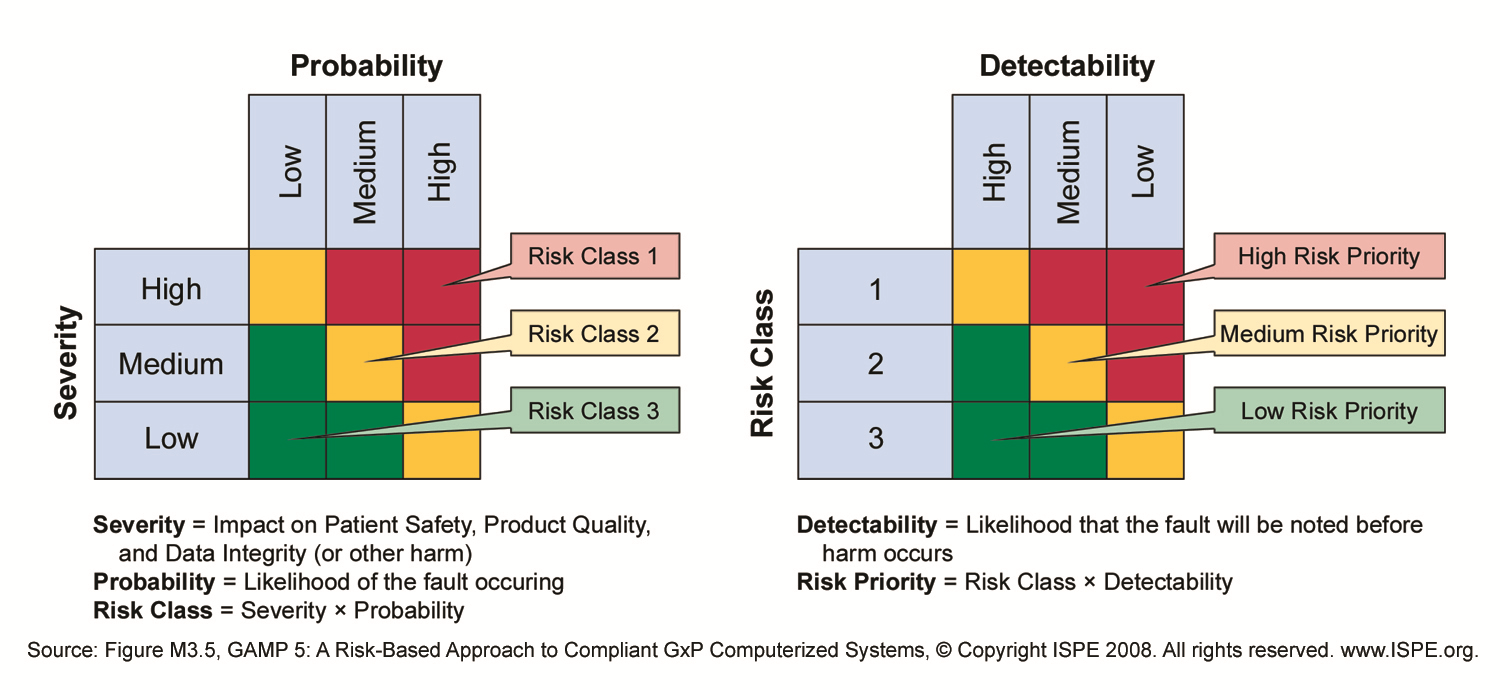
Cyber threats most certainly may impact product quality, patient safety and even data integrity. We incorporate these risks into our risk management profile to provide a more comprehensive risk assessment for computer systems.
ZDNet reports that “…As new security risks continue to emerge, cloud security spending will grow to $3.5 billion by 2021…”
ZDNet June 15, 2017
As life sciences companies increase their adoption of the cloud, new challenges for validate systems environment are emerging and the risks that go along with them. I wrote a blog post recently called “Validation as we know it is DEAD”. In this post, I addressed the challenges and opportunities that cloud and cybersecurity bring. Although cloud security “solutions” will driving spending by 2021, the solution is not necessarily a technology issue. You can attack cyber risks effectively with STRATEGY.
For validated systems environments, I am recommending a cybersecurity plan to combat hackers and document your level of due diligence for validated systems. Remember in validated systems, “…if its not documented, it didn’t happen…”. You must document you plans and develop an effective strategy for all of your computer systems.
Validation and risk are the power twins of compliance. Risk management cannot only facilitate the identification of controls to protect your systems long term, it can help ensure compliance and data integrity as well as drive efficiencies in your lean validation processes. In the conduct of your risk assessments, do not ignore cybersecurity risks – It is the elephant in the room.







