If you are a validation engineer reading this post, I have a simple question to ask you.. “How vulnerable is your validated systems environment?” Has anyone ever asked you this question? How often do you think about the impact of a cyber threat against your validated computer system? I know… you may be thinking that this is the IT departments responsibility and you don’t have to worry about it. THINK AGAIN!
If you have picked up in a newspaper lately you will see cyber threats coming from all directions. The White House has been hacked, all companies big and small have been hacked into and from the hacker’s perspective there seems to be no distinction between small medium or large enterprises. In summary, everyone is vulnerable. The definition of cyber security is the possibility of a malicious attempt to damage or disrupt a computer network or system.
Network applications continue to create new business opportunities and power the enterprise. A recent report suggested that the impact and scale of cyber-attacks is increasing dramatically. The recent leak of government developed malware has given cyber criminals greater capabilities than they had before. IT is struggling to keep pace with the flow of important software security patches and updates and the continuous adoption of new technologies like the Internet of things (IOT) that are creating new vulnerabilities to contend with.
A recent study in 2017 by CSO highlighted the fact that 61% of corporate boards still seasick security as an IT issue rather than a corporate governance issue. This is only one part of the problem. It is not even on the radar of most validation engineers. You cannot begin to confirm that a system meets its intended use without dealing with the concept of cyber security and its impact on validated systems.
Validated computer systems house GMP and quality information as well as the data required by regulators thus particular scrutiny must be paid to these systems. Compromise of a validated system may lead to adulterated product and issues which may affect the products quality efficacy and other critical quality attributes of marketed product. Therefore, attention must be paid to validated systems with respect to their unique vulnerability.
As part of the validation lifecycle process we conduct IQ, OQ, and PQ testing as well as user acceptance testing to confirm a system’s readiness for intended use. I am suggesting that another type of testing be added to the domain of validation testing which is called cyber security qualification or CyQ.
Cyber security qualification is confirmation of a system’s readiness to protect against a cyber attack.
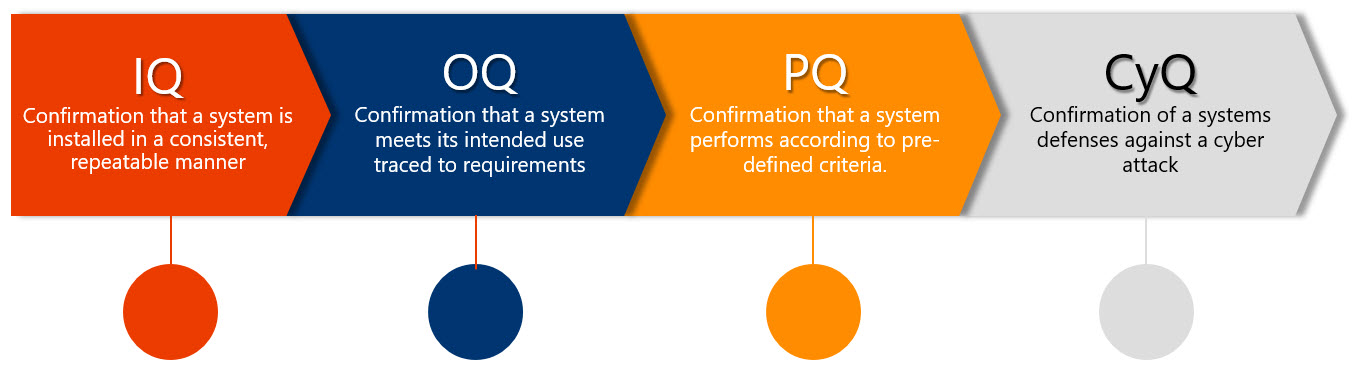
You should incorporate CyQ in your validation testing strategy. It is imperative that your validated systems are protected against a cyber event. You must document this as well to prove that you have conducted your due diligence. Given all of the attention to cyber events in the news, you need a strategy to ensure sustained security and compliance. Are you protecting your validated systems? If not, you should.







